
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
86-0769-39020536
In recent years, mobile applications have been extremely hot, and mobile Internet devices such as WeChat payment and Alipay payment parking fees have swelled in the parking lot, and the door-to-door industry, which is not too warm, has also emerged.
At present, there are four main solutions for mobile smart access control at the technical level: Bluetooth, NFC, QR code and WIFI. Let's take a brief analysis of the implementation and advantages and disadvantages of these four technologies.
Bluetooth technology
Technical background: Bluetooth technology is very mature, it is a wireless technology standard, which can realize short-distance data exchange between fixed equipment, mobile equipment and building personal area network (UHF radio waves using ISM band of 2.2-4.85GHz) ). Bluetooth technology was originally created in 1994 by the telecom giant Ericsson as an alternative to the RS232 data line. Bluetooth can connect multiple devices, overcoming the challenges of data synchronization.
Implementation: Bluetooth access control can be connected to the access control with a distance of about 8 meters without interference. The Bluetooth service is called by the app on the mobile phone, the intelligent hardware is installed at the access control end, and the door lock is controlled after receiving the Bluetooth command. .
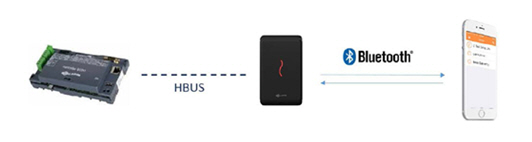
Gallagher Bluetooth Technology
advantage:
1. Mature technology;
2. The transformation cost is lower;
3. Long control distance;
Disadvantages:
1. The mobile phone needs to be turned on by the mobile phone;
2. If there is obstruction, it will affect the reading effect;
3. According to the analysis of TOP600 model data in May 2016, most of the smartphones support Bluetooth, but there are about 200 models supporting BLE Bluetooth 4.0, accounting for 33% of the mainstream models, that is, only 2015. The model launched in the year may support Bluetooth 4.0, and 67% of the models do not support BLE Bluetooth 4.0. Therefore, the popularity of Bluetooth access control is very large.
NFC technology
Technical Background: This technology evolved from contactless radio frequency identification (RFID), developed by Philips Semiconductors (now NXP Semiconductors), Nokia and Sony, based on RFID and interconnect technology. Near Field Communication (NFC) is a short-range high-frequency radio technology that operates at a distance of 10 cm at 13.56 MHz. The transmission speed is 106 Kbit/s, 212 Kbit/s or 424 Kbit/s. At present, near field communication has passed the ISO/IEC IS 18092 international standard, the ECMA-340 standard and the ETSI TS 102 190 standard.
Implementation: First, you need a mobile device with NFC capabilities. Second, you need to configure the hardware that can read the virtual credential card from an NFC-enabled mobile device. Finally, an ecosystem must be developed that includes mobile network operators, trusted service managers, and other operators that provide and manage mobile credential cards.

NFC access control
advantage:
1, the setting procedure is shorter, using NFC instead of manual setting will greatly speed up the creation of the connection: less than one tenth of a second;
2, low power consumption, only one machine link at a time, with a high degree of confidentiality and security.
Disadvantages:
NFC-enabled phones are less than Bluetooth 4.0, accounting for about 15.4%. Therefore, NFC is good, but it is only suitable for specific occasions.
QR code technology
Technical background: 2-dimensional bar code is a black and white graphic that records data symbol information in a plane (two-dimensional direction) with a certain geometry according to a certain rule; The concept of "0" and "1" bitstreams that make up the internal logic of the computer is skillfully used, and several geometric shapes corresponding to binary are used to represent the literal numerical information, and the image input device or the photoelectric scanning device automatically recognizes Read to achieve automatic processing of information; it has some commonality of bar code technology: each code system has its own specific character set; each character occupies a certain width; has a certain check function. At the same time, it also has automatic recognition function for different rows of information, and handles the rotation change point of the graphic.
Implementation: QR code access control uses two-dimensional code as the medium and carrier for personal identification. The system assigns each user a real-time encrypted QR code. The user can scan the QR code on the access control device to open the corresponding Door lock.

QR code access control
advantage:
1. The current application of QR code is very wide, and it is convenient and easy to use, which is conducive to popularization;
2. The two-dimensional code can integrate two functions of access control management and visitor management.
3, whether using the APP or the public number, can support most smartphones;
4. User experience is better.
Disadvantages:
1, the QR code is easy to be copied, there are security risks;
2. The cost of transformation is relatively high.
WIFI technology
Technical background: Wireless network technology was invented by the Australian government research institute CSIRO in the 1990s and successfully applied for wireless network technology patents in the United States in 1996. Almost all smartphones, tablets and laptops support Wi-Fi Internet access and are the most widely used wireless network transmission technology today. WIFI is not affected by the hardware chip and operating system, the connection speed is fast, it can be connected one-to-many, and it can also directly connect to the Internet. The WIFI protocol implements the globally compliant standard 802.11n protocol, which is forward-looking and has been released since then. It has never been replaced, and there is no compatibility problem. It is suitable for all mobile phones.
Implementation: It is widely used in the smart community. It is usually used together with monitoring and access control through APP.

Wifi open
advantage:
1, using WIFI access control, usually one of the applications of the smart community, compatibility, large capacity, and rich features;
2, the communication protocol is a unified standard 802.11n, all smart phones can be stable and applicable;
3, the background management is convenient, and can be opened remotely.
Disadvantages:
1, need to access the network, the cost of transformation is higher;
2, WIFI access control is highly dependent on the network, if there is a phenomenon of network disconnection, unstable network signal transmission, etc., it will directly affect the application of this function.
March 08, 2024
November 29, 2023
อีเมล์ให้ผู้ขายนี้
March 08, 2024
November 29, 2023

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.